Introduction – What is SSH?
Secure shell (SSH) was introduced about 6 years after the World Wide Web (made by the great Tim Berners-Lee!) and is an encrypted method for sending data over an insecure network.

Initial connection setup is kept secure as the process uses public key cryptography to verify the identity of the SSH server. Parameters such as the symmetric encryption algorithm is negotiated between the client and server during this setup process.
An extensive documentation is provided:
- https://www.ssh.com/academy/ssh/protocol
- (The SSH company was founded by the person who invented SSH – Tatu Ylönen)
The site also contains RFCs for the SSH protocol:
- RFC 4251, 4252, 4253, 4254
Local Port Forwarding
The simpler technique out of the two, data is forwarded to a server through an intermediary server (sometimes known as a jump host). Typically, a use-case for local port forwarding is for accessing internal company services on an external network:

This technique creates an encrypted connection between the client and the server, allowing you to securely access internal services.
Remote Port Forwarding
This technique (similar to local port forwarding) still creates an encrypted connection between the client and server but the process for this differs from local port forwarding:
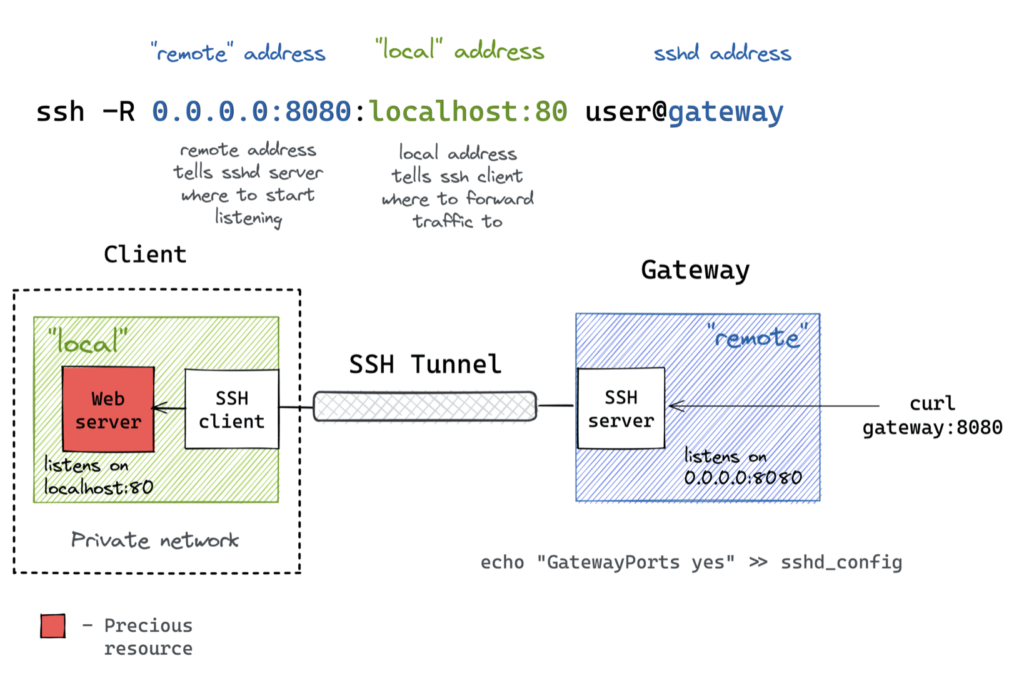
Note: The command :
- <
echo "GatePorts yes" >> sshd_config>
This is used when you don’t want to bound the gateway address to localhost. If you want to use the gateway’s public address then the provided command needs to be entered.
Here, traffic is forwarding from the remote server to the client. This method allows external services to services running on your client device via an SSH tunnel.
A use-case for this is if you are deploying a mobile application on your device and you want to share it with a customer without deploying a public server, remote port forwarding will allow the customer to access the mobile application securely.
Conclusion
It depends on your use case whether you should use local port forwarding or remote port forwarding as they both provide different functionalities. Typically though, it is more difficult to setup a remote port forwarding service as there are further security considerations. If not setup correctly, a threat actor can potentially setup a backdoor to your server.