Introduction
Today, I came across a strange phenomenon whilst looking at a troubleshooting scenario:
- https://sadservers.com/newserver/taipei
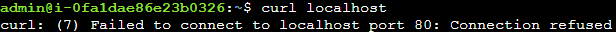
Connection refused on port 80, nothing too interesting. However, when I was looking for other open ports using nmap I tried the same test again:
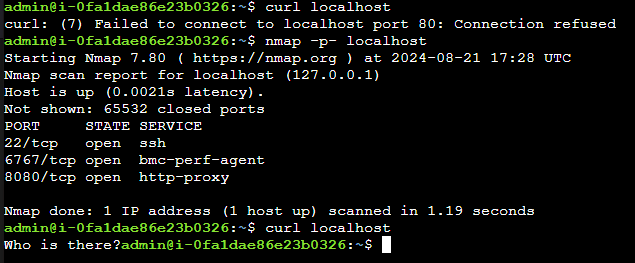
Now how is that possible? This is all because it had been protected using Port Knocking.
What is Port Knocking?
Port Knocking is a security technique used to control access to a network service that would otherwise be closed / hidden.
To open up these services, you would need to generate a connection attempt (or “knocks”) on a series of ports before the desired port is open. Only people who know these knocks can access the actual desired port.
How Port Knocking Works
The steps for Port Knocking is as follows:
- Close desired port
- The target service’s port is closed so that it is inaccessible to all users.
- Knock Sequence
- User sends a sequence of connection attempts (knocks) to a predefined set of ports.
- Can be TCP, UDP, or even ICMP packets depending on the implementation.
- Authentication and Verification
- A daemon or firewall on the server listens to the knocks. If the correct of sequence of knocks is detected, then the desired port is temporarily opened for the user’s IP address.
- Access
- The user can now access the desired network service.
- Automatic Port Closing
- Once connection is closed, or after a short period the port is closed again.
Conclusion
Port Knocking is a clever way to increase security, adding an additonal layer of security to your system. However, it should not be the only layer of security and should be configured correctly. As shown in my example I was able to access the hidden service by accident from only a nmap scan which was sufficient “knocks” to gain access.