Background
Burp Suite is an essential tool for web penetration testing and one module they provide is Burp Proxy, an intermediary proxy that rests between your client browser and web application.
This proxy is nifty as you’re able to intercept any HTTP(S) requests and modify them to your liking, this modified traffic can then be forwarded as normal to the web application.
Downloading Burp Proxy
I’m currently using Kali (https://www.kali.org/tools/burpsuite) and the download process is very simple with a single command:
sudo apt install burpsuite
Once installed onto my system, the next step is to configure the proxy.
Configuring Burp Proxy listener
By default, the Burp Proxy = listener sits on localhost port 8080:
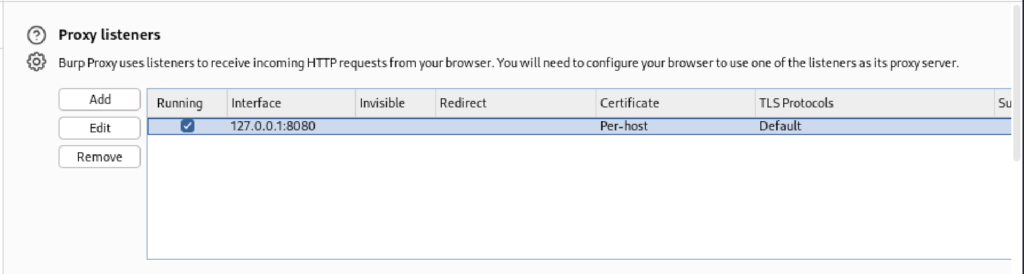
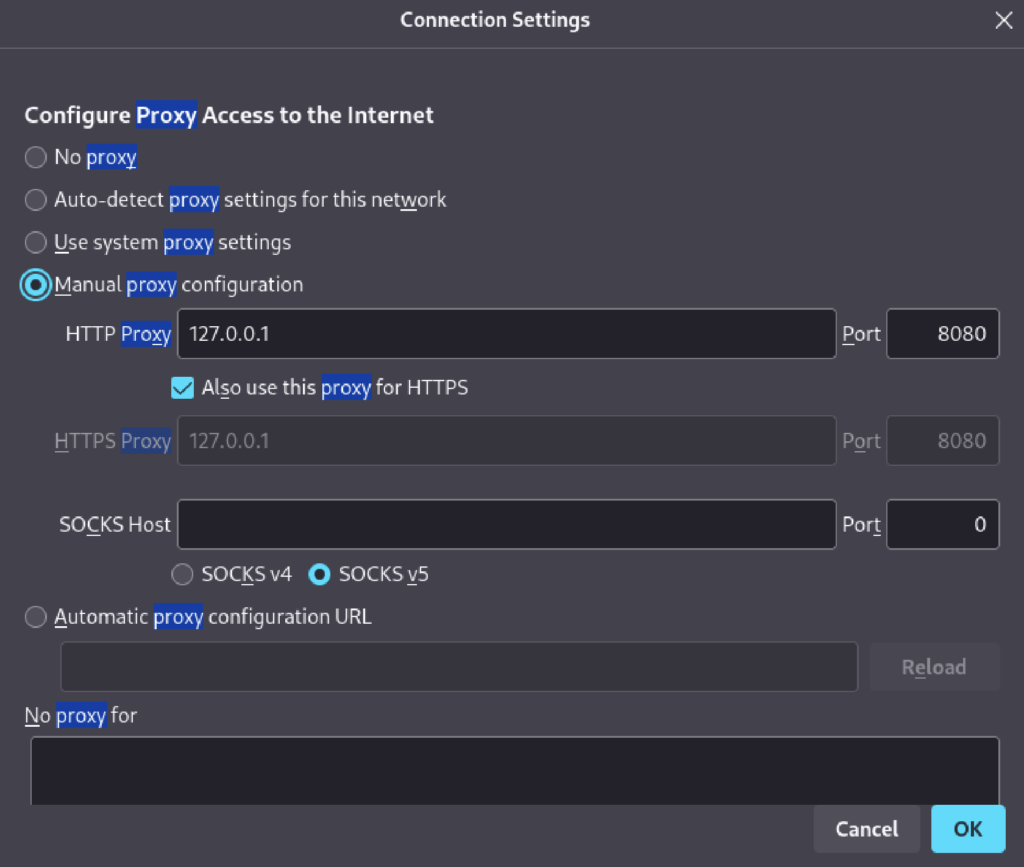
The next step is to configure the browser’s proxy settings to route through Burp Proxy:
Let’s verify by accessing our proxy (typing http://burp or http://burpsuite should work):
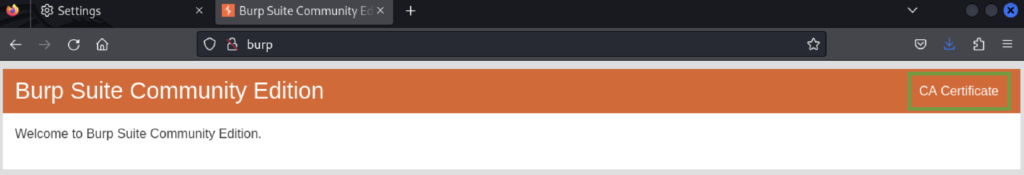
This is also an important step as you’ll be able to download a CA certificate (to prevent security warnings when accessing a HTTPS site) from the green square highlighting from the screenshot above.
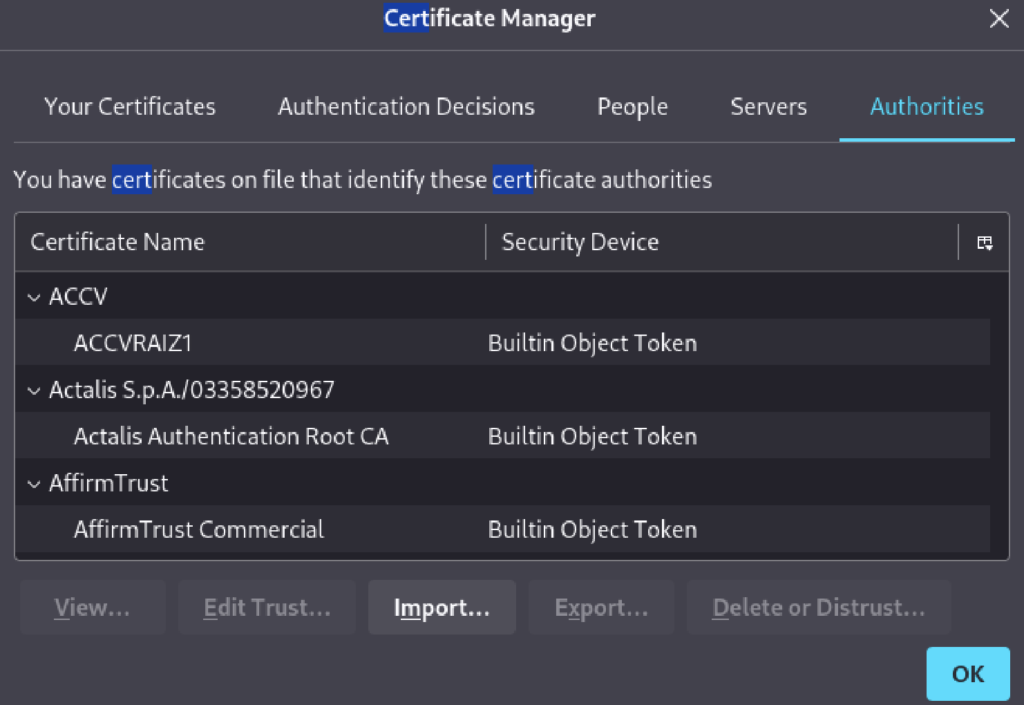
After importing the CA certificate, I can test if my HTTP(S) traffic is being routed through Burp Proxy:
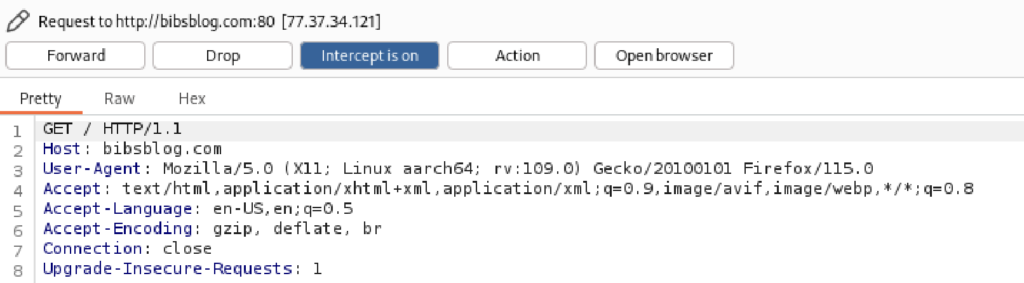
Conclusion
A simple guide on setting up Burp Proxy, from here I can either decide to forward the request, drop it or even modify my request before forwarding it.