A simple open-source scanner to detect IOCs
Loki Overview
Uses 4 methods of detection:
- File name IOC
- Regex match on full file path/name
- YARA rule check
- YARA signature match on file data and process memory
- Hash check
- Compares hash of file with known malicious hashes
- C2 Back Connect check
- Compares process connection endpoints with C2 IOCs
Loki comes with some pre-defined YARA rules that are stored within /signature-base/yara. Perusing through this directory you will be able to identify some very well known threats. For example there is a YARA rule to identify the ransomware NotPetya:
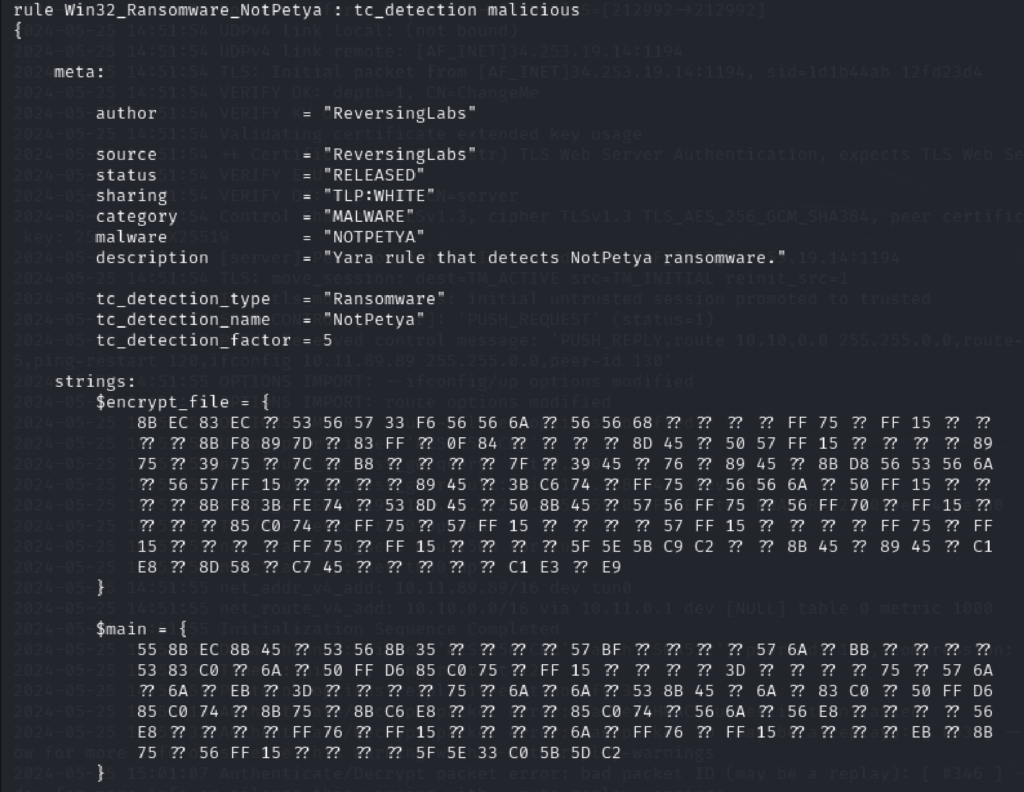
Win32.Ransomware.NotPetya.yaraOverview of YARA
The full explanation behind the hexadecimal string values determined for this YARA rule is more in the scope of in-depth malware analysis. However, to give a quick run-down of how YARA works:
- Create rule name
- In this example, rule is
Win32.Ransomware.NotPetya.yara
- In this example, rule is
- Provide any metadata
- This will give more detail about the rule itself, i.e. the author and a description about the rule
- Create string(s)
- This is where patterns, signatures or strings are defined. YARA rule will look for these string values in the file(s) or network(s)
- In this case, there are several string patterns for example
encrypt_file
- Condition
- This statement will identify if the YARA rule matches with the file you’re scanning:
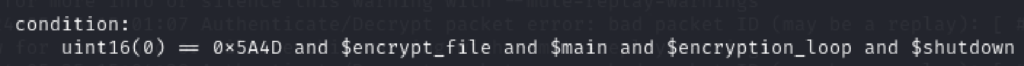
Win32.Ransomware.NotPetya.yaraLoki Detection
I have two potentially malicious folders:
My objective is to detect if any files within these folders are suspicious:
python /home/<user>/tools/Loki/loki.py -p .- Loki will scan and identify any IOCs in the files
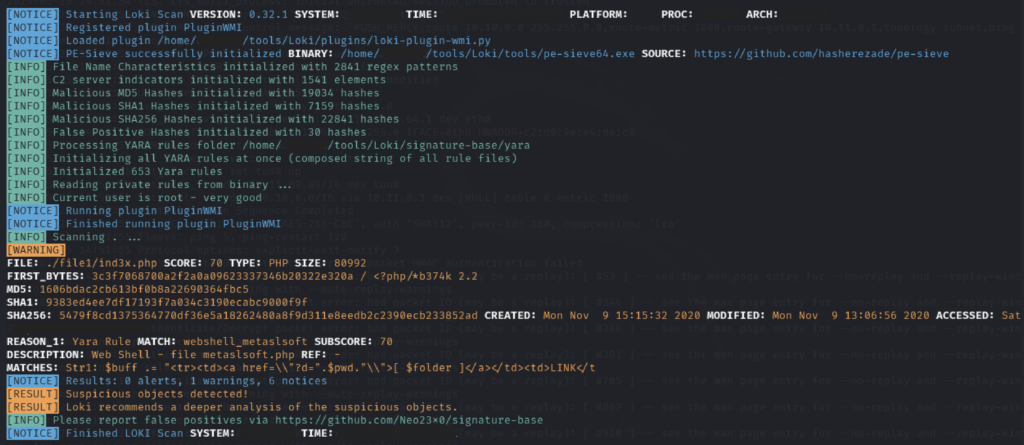
file1!Overall Yara is a very simple but good tool to detect IOCs, however as shown from the Loki result, it does recommend a deeper analysis of any objects identified as suspicious.
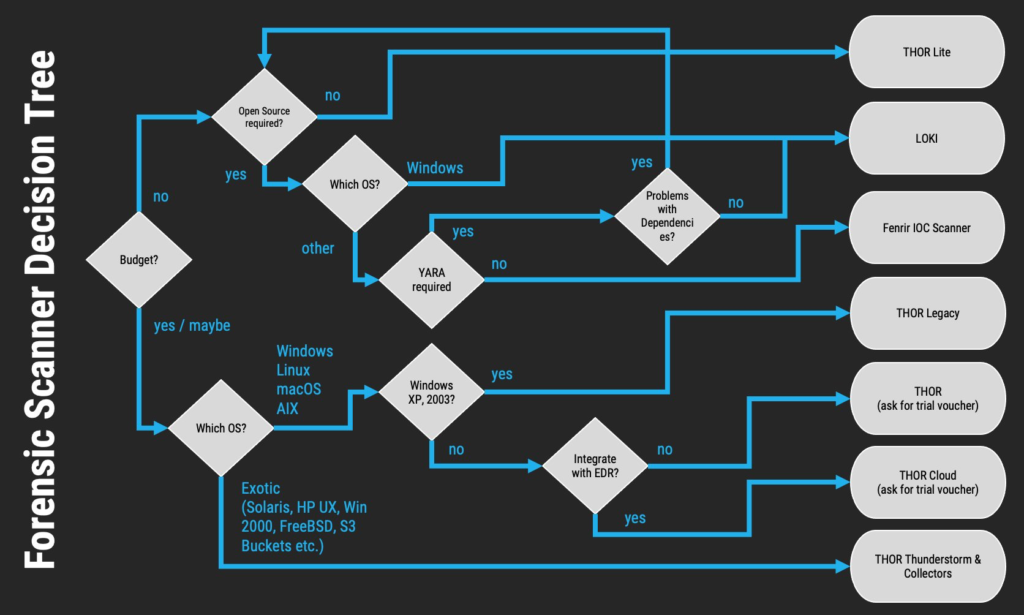
The creator “Florian Roth” has been working on more sophisticated tools which can be found in the Github provided above. Florian has also provided a simple flowchart to identify which tool to use: